McAfee raises the alarm: in these hours it is hitting several countries including Italy and Israel. The malware is delivered through a UEFI implant, the same one used in the past by Hacking Team
tal
In a recent tweet by Raj Samani, Chief Scientist at McAfee, it is discovered that the MosaicRegressor malware is currently hitting several countries, including Italy. The sectors under attack are unknown, as are those behind the cyber offensive. This is even though some cybersecurity analysts believe they may be hacker groups linked to China. The only consolation is that we are in good company, with us there are:
- United States
- Hungary
- Estonia
- Israel
- India
- Belgium
- Ukraina
- South Africa
Moreover, the fact that Israel is among the targets has its own relevance, in the same way that the attack vector is UEFI implants, well known as widely used by Hacking Team, the Italian cybersecurity company that sold spyware in all over the world and which was destroyed years ago by unknown persons.
What are UEFI Implants
Perhaps not everyone knows what UEFI means: it is an acronym that stands for “Unified Extensible Firmware Interface” and is a technology whose “software” resides in the hardware of the computer itself. It takes care of turning on the PC, checking the operation of all peripherals, interacting and launching the operating system. Summarizing a lot, we can say: it is a specification that defines the low-level operational structure of a system, a feature-rich environment, with which one can interact while the computer is on and running. So, paradoxically, it is an “unchangeable” component dedicated to the start of the PC, which can instead be “modified” in its modules through the interface: for this reason it has begun to be targeted by cybercrime groups in order to create attacks of a persistent nature. The persistence of infected UEFI is due to the fact that they reside in the computer hardware.
The persistence is given by the fact that an infected UEFI cannot be “disinfected” by the classic antivirus and not even by the most drastic of operations: the reinstallation of the operating system from scratch or the replacement of the hard disk. This is because the “virus” now resides in the computer hardware. At the moment, there are a couple of cases of this type of “implant”, as they are defined in the jargon. One of these “public” discoveries is dated 2018 and has the name of LowJax, discovered by ESET cybersecurity experts, which was used by Sofacy (aka FancyBear) to infect a number of users.
The destruction of the Italian Hacking Team led to the discovery of its weapons and in particular of the UEFI implant VectorEDK
When Hacking Team, the Italian company that sold spyware all over the world, was attacked and destroyed, all its exploits were publicly revealed thanks to the dissemination of the source code of its weapons. The world also got to know VectorEDK, another UEFI Implant. This code consists of a series of UEFI modules, which, embedded in an original and benign UEFI, can instead install a “backdoor” every time the computer starts: this allows a malicious actor to enter precisely through the “back door” of a device and spy on whatever is being done on the PC. Private messages, mail, images, conversations, confidential documents, everything becomes visible to the invisible eye of spyware. Someone is using the UEFI modules of the Italian cybersecurity company to inject the MosaicRegressor malware into the target computers.
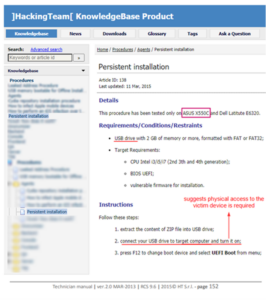
The blatant news is that these Hacking Team UEFI “modules” are obviously still available and usable on the Internet, so much so that anyone can download them, modify them and make them poisonous again. It would seem, in fact, that someone has already done so: and it was thus that the Kaspersky researchers identified a “slightly” modified clone of the exploit of the Italian cybersecurity company, as reported in an excellent study (for insiders and very technical cut) of a few days ago. The “new” UEFI Implant, this time, instead of infecting the victim with the old spyware of Hacking Team (Soldier ‘,’ Scout ‘or’ Elite ‘) now uses “MosaicRegressor”. It is interesting to note that on the Internet you can still find the “user manual” used at the time by Hacking Team to guide its “consultants” in installing a “Persistent Installation” of their Implant. Kaspersky’s suspicion, however, is that an updated version of this “implant” could exploit an unidentified “remote” infection capability.
What is MosaicRegressor malware
MosaicRegressor is the usual multistage and modular framework, aimed at spying and data collection. It consists of “downloaders” and, occasionally, multiple intermediate loaders, which are intended to retrieve and execute payloads on the victim’s computers. The fact that it is made up of multiple modules helps attackers to hide it more easily from cybersecurity researchers who study the binary code of malware, as well as to distribute components on target machines only when needed. Thus it happens that, even if discovered on a device, it is not possible to take possession of all its components, but only of some parts. That is to say those that were “shot” at that victim. For example, depending on the need to spy on Whatsapp or Telegram conversations, the malicious code also “loaded” this feature. Was it necessary to steal his Facebook credentials or steal his access to the bank? It was enough to download the ad hoc form. In other words, these frameworks have modules for every need that are “sent” to the victim according to the needs of cybercrime. Furthermore, according to what the Kaspersky study says, it seems that the victims of this malware include diplomatic personalities and members of non-governmental groups, attacked from 2017 to 2019 in Africa, Asia and Europe.
The author
Odisseus is one of the least aligned cybersecurity experts in Italy: he has many scoops and interviews in national newspapers and is known for his critical positions in general towards the national strategy on cybersecurity. He frequents industrial and university circles just enough to remember to stay away from them.
By Francesco Bussoletti (Italian), October 16, 2020, Published on Difesa and Sicurezza
Pic By Hacking Team – www.hackingteam.it, Public Domain






