During June-August of 2020, ClearSky’s analysis team had investigated an offensive campaign attributed with high probability to North Korea, which we call “Dream Job”. This campaign has been active since the beginning of the year and it succeeded, in our assessment, to infect several dozens of companies and organizations in Israel and globally. Its main targets include defense, governmental companies, and specific employees of those companies.
We assess this to be this year’s main offensive campaign by the Lazarus group, and it embodies the sum of the group’s accumulative knowledge on infiltration to companies and organizations around the globe. In our estimation, the group operates dozens of researchers and intelligence personnel to maintain the campaign globally.
Throughout the campaign, the North Korean “Lazarus” group (aka HIDDEN COBRA) succeeded in manipulating the targets with a “dream job” offering, which was sent to the employees of said targets. The “dream job” is supposedly sent on behalf of some of the most prominent defense and aerospace companies in the US, including Boeing, McDonnell Douglas, and BAE.
The infection and infiltration of target systems had been carried out through a widespread and sophisticated social engineering campaign, which included: reconnaissance, creation of fictitious LinkedIn profiles, sending emails to the targets’ personal addresses, and conducting a continuous dialogue with the target – directly on the phone, and over WhatsApp. Upon infection, the attackers collected intelligence regarding the company’s activity, and also its financial affairs, probably in order to try and steal some money from it. The double scenario of espionage and money theft is unique to North Korea, which operates intelligence units that steal both information and money for their country.
In 2019, we have revealed evidence of Lazarus’ attack in Israel, whereas the North Korean espionage group had attempted to infiltrate the network of an Israeli defense company, and since this attack we have been monitoring the group’s activity in Israel. In recent months, we have succeeded in identifying new indications of the group’s activity in Israel.
This report’s main findings include:
-
Social engineering chapter, which presents the stages to targets’ infection and the social engineering tactics used to manipulate it.

-
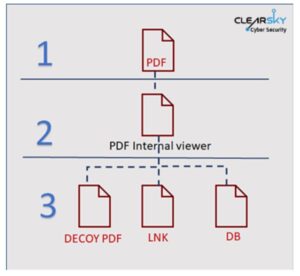
Offensive tools’ analysis chapter, which surveys the three infection scenarios in this campaign:
-
Infection through a malicious PDF file in an open-source PDF reader, which was altered to fit the group’s needs. This is the first time this scenario is revealed publicly.
-
Infection through a Dotm file, which is downloaded from a breached server, takes the place of the original file, and runs a malicious macro on the target
-
Infection through a Doc file containing a malicious macro.
Read the full report: Operation ‘Dream Job’ Widespread North Korean Espionage Campaign
By ClearSky Research Team, August 13, 2020, published on clearskysec.com
Image by Cleo Robertson from Pixabay






