Researchers analysing the collateral consequences of a ransomware attack include costs that are roughly seven times higher than the ransom demanded by the threat actors. This includes the financial burden imposed by the incident response effort, system restoration, legal fees, monitoring costs, and the overall impact of business disruption.
Ransomware attacks typically involve stealing data from the company and encrypting systems to pressure the victim into paying to decrypt files and to avoid a data leak.
Researchers at Check Point compiled ransomware statistics by analysing data from public sources and several thousand cyber attacks in the Kovrr database, a cyber-risk and cyber-insurance expert.
.
Setting the ransom demand
Starting with the amount of the ransom, the threat actors appear to follow a specific pattern based on the victim’s financial records to establish how much to ask.
.
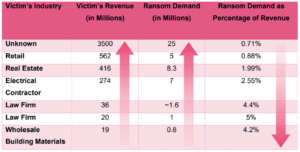
Setting a ransom demand based on firm revenue
According to Check Point’s analysis, the ransom demand is typically between 0.7% and 5% of the victim’s annual revenue, with the average percentage being 2.82%.
Many ransomware gangs offer discounts for fast payments, ranging between 20% and 25% if the ransom is paid within a few days.
.
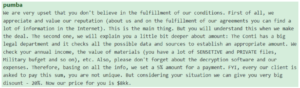
Conti’s negotiator offering discount and explanations
.
Estimating the impact
The overall impact of a ransomware attack on an organisation’s financials is directly linked to the duration of the incident, from encryption to full system restoration.
In 2021, organisations demonstrated a better ability to handle the double-extortion tactics, which reduced the attack duration significantly..
.
.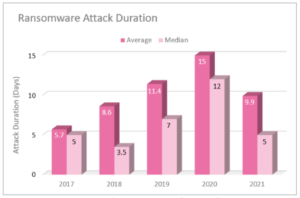
Duration of ransomware attacks
However, this double-extortion tactic introduces additional cost for the victimised organisation, which now has to deal with their customers losing trust and long-term reputational damage.
When hit by ransomware, the victimised entity has to cover the cost of lost income from business disruption, legal procedures, incident response and remediation, malware discovery and deletion, restoring data from backups, contracting third-party experts, and more.
.
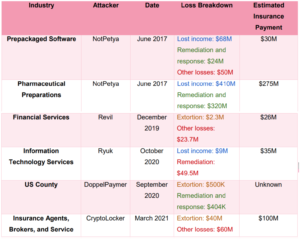
Financial impact on ransomware victims
Even if the organisation pays the ransom, there’s no way to avoid further financial losses, and restoring systems using the decryption keys from the attackers is often slower than using backups.
“Most other losses, including response and restoration costs, legal fees, monitoring costs, etc., are applied whether the extortion demand was paid or not. The year 2020 showed that the average total cost of a ransomware attack was more than seven times higher than the average ransom paid.”
Preventing the incidents from happening in the first place is the most crucial element, far more critical even than relying on the most advanced incident response system.
.
From the actor’s perspective
Ransomware gangs and operators of large ransomware-as-a-service (RaaS) programs understand the delicate economic balance that comes into play and take measures to keep payment the most practical option.
What they do is link the ransom payment to the collateral damage costs when negotiating with the victim, presenting the payment option as a more financially beneficial option.
.
.
In fact, ransomware actors often bring up the collateral damage costs in negotiations, like, for example, using GDPR violation fines (due to customer data leak) as an extortion argument.
Despite all the law enforcement action against these threat groups, and the evolution of defence tactics, ransomware continues to proliferate and break new records.
Both attackers and defenders are adjusting to new realities imposed by an ever-evolving landscape, and neither can afford to fall behind in this race.
.
April 28, 2022 Published by The Bleeping Computer.







